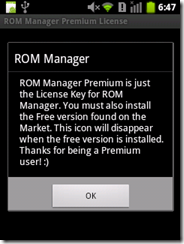
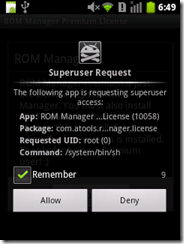
| NQ Mobile Security Research Center has recently uncovered a new malware –DKFBootKit. This malware is identified when monitoring and analyzing the evolution of earlier DroidKungFu variants. While it uses known techniques to piggyback malicious payloads into legitimate apps, it intentionally chooses legitimate apps that require root privilege to facilitate its payload. Specifically, by taking advantage of the root privilege, DKFBootKit adds itself as a part of the boot sequence of the original Android system and replaces a number of utility programs (e.g., ifconfig and mount). By doing so, the malware can get started even before the entire Android framework is bootstraped. To the best of our knowledge, this malware is the first of its kind in moving towards a full-fledged bootkit on Android, which represents a serious threat to mobile users. Based on our initial investigation, we have so far identified more than 100 infected malware samples and it seems this number continues to grow at the time of writing this report. HOW IT WORKS? Based on our analysis, DKFBootKit repackages legitimate apps by enclosing its own malicious payloads in them. However, the victim apps it chooses to infect are utility apps which require the root privilege to work properly. In the samples we analyzed, the infected apps range from ones managing apps installed on the phone, unlocking popular games, to others providing the license keys for some (premium) paid apps. These apps seem to have legitimate reasons to request root privilege for their own functionality. It is also reasonable to believe that users will likely grant the root privilege to these apps. However,DKFBootKit makes use of the granted root privilege for other malicious purposes, namely comprising the system integrity. We believe DKFBootKit is much more stealthy than the earlier DroidKungFu variants, which rely on existing exploits to gain root privilege. In the following, we show a screenshot of one DKFBootKit-infected sample that intends to provide the license key for a paid version of ROM managent app. Based on our study, DKFBootKit adds a common background service to victim apps, which once run will release a hidden executable program. This hidden program will check whether it has the root privilege. If not, it terminates itself. Otherwise, it mounts the system partition as writable, copies itself into the /system/lib directory, replaces several commonly-used utility programs (e.g.,ifconfig and mount), and alters related daemons (e.g., vold and debuggerd) and bootstrap-related scripts. The purpose seems to allow itself to run earlier than the Android framework is initialized to start other apps. Moreover, the malware itself contains a bot payload that phones home to several remote C&C servers and waits for further commands. It's worth mentioning that becauseDKFBootKit utilizes the root privilege, it can execute arbitrary commands. We are still in the process of actively monitoring DKFBootKit C&C servers. An initial investigation of these C&C servers show that the related domains were registered in January, 2012. Mitigation: Due to the fact that DKFBootKit utilizes the root privilege and can be remotely controlled to install or remove apps without user's knowledge, we believe it poses serious threats to mobile users. To avoid becoming a victim, please follow common-sense guidelines for smartphone security: 1) Only download applications from trusted sources, reputable application stores, and markets, and be sure to check reviews, ratings and developer information before downloading. 2) Never accept application requests from unknown sources. Closely monitor permissions requested by any application; an application should not request permission to do more than what it offers in its official list of features. 3) Be alert for unusual behavior on the part of mobile phones and be sure to download a trusted security application that can scan the applications being downloaded onto your mobile device. NQ Mobile Security users are already fully protected from the "DKFBootKit " threat. NQ Mobile Security for Android is available for download at http://www.nq.com/mobilesecurity and on Android Market. Source: NQ Mobile Security Center Stay Safe.. Hv gr8 day! | |||
| | |||
| | |||
|
Saturday 31 March 2012
DKFBootKit Malware- First Android BootKit
Subscribe to:
Post Comments (Atom)


No comments:
Post a Comment